Security Alert: Plugin Flaw Puts Over 200K WordPress Sites At Risk

If you run a WordPress-powered site, then you must get to know it!
A high-severity cross-site request forgery (CSRF) to Remote Code Execution (RCE) vulnerability, tracked as CVE-2020-8417, has been discovered in a popular WordPress plugin, potentially opening up over 200K websites to complete takeover, information disclosure, and more.
The plugin in question is Code Snippets, which offers users an intuitive graphical user interface (similar to the Plugins menu) to add, run and manage PHP code snippets to their WordPress sites in order to customize or extend the functionality of the website, all without diving into the theme’s underlying code.
The flaw was first discovered by the Wordfence threat intelligence team on January 23rd. According to researchers, this WordPress vulnerability is so severe and easy to exploit that hackers could hijack your entire site within a matter of minutes.
The Problem:
Code Snippets offers a menu that enables users to import small chunks of PHP code onto the websites. However, researchers discovered that the plugin’s import menu had a missing referrer check, allowing a web page to see the origin of requests. This leads to the activation of malicious code on import, opening the affected site up to cross-site request forgery (CSRF) attack.
As per the Wordfence threat intelligence team, the flaw allows hackers to forge a fake request on behalf of the administrator, inject malicious codes on the vulnerable site and execute them remotely. Surprisingly, the attacker was also able to create a new administrator account, access and extract sensitive data, infect site users, and much more.
Even, to help you understand how the arbitrary code could be injected and executed on a vulnerable site, experts have published a video proof of concept of the vulnerability as well.
Wordfence researchers further explained that the plug-in developer had taken all the security measures possible to protect nearly all endpoints of the plugin with WordPress nonces, except the import function that is vulnerable to CSRF. This is indeed a high severity security issue as the plugin is installed on over 200,000 sites.
The Solution:
Thankfully, a couple of days after the flaw was discovered, the plugin’s developer released a patch to fix CSRF-RCE, which is now available as version 2.14.0. Any website owners running an older version of the plugin have been recommended to update the plugin to the latest version (2.14.0) immediately.
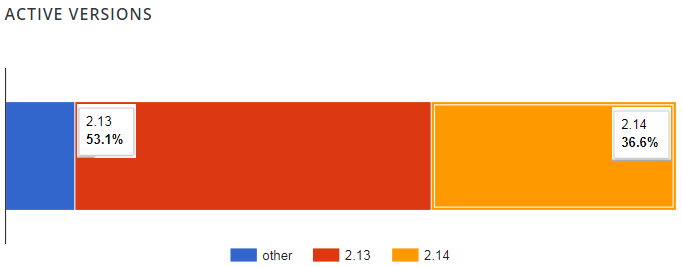
According to official plugin statistics, only 36.6% of users have downloaded and installed the latest version, while 53.1% are still on the older version and exposed to attacks.
If you fall in the latter category, update the plugin to the patched version as soon as possible. In case your WordPress site has got affected or hacked due to the older version of the plugin, feel free to hire highly skilled and certified WordPress Developers from WordPressIntegration to fix all the issues.